Last year saw the arrival of the Apple-curated Mac App Store, a creation very much in the mold of the iOS App Store. And many people wondered: Would a locked-down version of Mac OS X, one incapable of running apps not approved by Apple, be far behind?
 Apple certainly could have done something like that with Mountain Lion, the company’s planned update to Mac OS X that should arrive this summer. But it hasn’t—instead, the company has created a new way for developers to sign their work and a new set of options in the Security & Privacy preference pane. According to Apple, it’s all an attempt to improve Mac security. Here’s how the new Gatekeeper feature works.
Apple certainly could have done something like that with Mountain Lion, the company’s planned update to Mac OS X that should arrive this summer. But it hasn’t—instead, the company has created a new way for developers to sign their work and a new set of options in the Security & Privacy preference pane. According to Apple, it’s all an attempt to improve Mac security. Here’s how the new Gatekeeper feature works.Check before first launch
Since at least the days of version 10.5, OS X has had a feature called File Quarantine, which checks apps before they run for the very first time. You most often encounter this feature when you download an app and run it for the first time—a dialog box appears informing you that it’s a file downloaded from the Internet, and asking for you to confirm that you do indeed want to run it. (This feature only works with files downloading by certain apps, including web browsers and email clients. A file copied from a USB drive or from a network volume doesn’t get checked.)
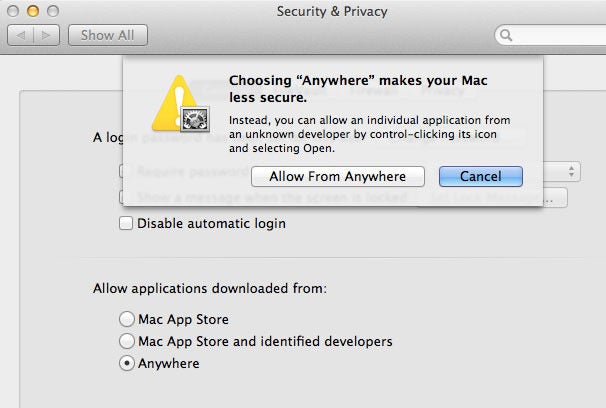
Gatekeeper uses this same feature. Instead of just asking you for permission to launch an app for the first time, Mountain Lion will check its security settings to see what sorts of apps are allowed to launch. Located in the General tab of the Security & Privacy preference pane is a setting called “Allow applications downloaded from,” with three options:
Anywhere: This choice uses the same set of rules as every previous version of Mac OS X. If an app isn’t known malware and you approve it, it opens.
Mac App Store: When this choice is selected, any apps not downloaded from the Mac App Store will be rejected when you try to launch them.
Mac App Store and identified developers: This is the new default setting in Mountain Lion. In addition to Mac App Store apps, it also allows any third-party apps that have been signed by an identified developer to run.
Identified developers
So what’s an “identified developer?” Basically, it’s any developer who registers as a developer with Apple and receives a personalized certificate. The developer can then use that certificate to cryptographically sign their apps. Any such app has two important characteristics: Apple can tell who developed it, and Mountain Lion can detect whether it’s been tampered with since it left the hands of the developer.
The first part is important because, Apple says, if a particular developer is discovered to be distributing malware, Apple has the ability to revoke that developer’s license and add it to a blacklist. Mountain Lion checks once a day to see if there’s been an update to the blacklist. If a developer is on the blacklist, Mountain Lion won’t allow apps signed by that developer to run.
When you try to launch an app using this system, your Mac will check with Apple’s servers to see if the developer’s signature is current. But what it doesn’t seem to mean is that previously-installed malware will be wiped clean, because once an app passes File Quarantine and launches successfully for the first time, it’s basically escaped Apple’s screening system.
The fact that Mountain Lion can detect apps that have been modified since they were signed is relevant because while there’s not a lot of Mac malware out there, what does exist is largely based on legitimate apps that have been modified to include malware and then redistributed on piracy sites. With this new model, any tampering with an app would render it unlaunchable.
Given the scrutiny that Apple puts apps through as a part of the App Store screening process, it’s important to note what the “identified developer” program doesn’t do.
It’s not a background check for developers. Getting a developer certificate isn’t like getting a passport or a driver’s license. A developer signs up for an account and gets a certificate. That’s it. What’s more, these apps have no seal of approval from Apple. Apple never sees them. Developers don’t need to check with Apple before signing apps. Apple’s not involved other than providing them with a certificate that Apple can revoke later if it feels the developer is distributing malware.
Gatekeeper’s limitations
 If you want Mountain Lion to run every app under the sun, you can just change the setting to Anywhere. (Changing this setting requires that you enter an administrator’s user name and password.)
If you want Mountain Lion to run every app under the sun, you can just change the setting to Anywhere. (Changing this setting requires that you enter an administrator’s user name and password.)Gatekeeper is also really easy to override. If you right-click on an app in the Finder and then choose Open, you’re prompted with a different dialog box—one that also offers to open the offending app. If you choose Open, the app launches normally, and that’s it.
Finally, it’s important to note that because Gatekeeper uses the File Quarantine system, it only worksthe very first time you try to launch an app, and even then only when it’s been downloaded from an app on your Mac like a web browser or email program. And once an app has been launched once, it’s beyond the reach of Gatekeeper.
Combine this with the ease of overriding Gatekeeper by using the Open command and it’s clear that Gatekeeper in Mountain Lion isn’t intended to be some sort of high-security app lockdown. It’s just a tool to encourage people not to run software they don’t trust. If they really, truly want to run an app, Mountain Lion won’t stop them.
For more Macintosh computing news, visit Macworld. Story copyright © 2011 Mac Publishing LLC. All rights reserved.

No comments:
Post a Comment